How can access control optimize security in higher education? How can it empower administrators and safeguard users while delivering economies? Research by HID Global and Genetec suggests that access control is becoming embedded in general security systems and that safety technology can influence where a student chooses to study.
HID Global commissioned www.SecurityInformed.com to produce a survey, researching this question.
Despite the high profile of access control, legacy technologies predominate across education. More than half of respondents said they still use mag stripe while almost a quarter continue with 125khz Prox. Older systems such as barcode and 125kHz low-frequency remain widespread. But benefits of smart cards and even mobile access are well known.
The survey indicates that the next two years will see many system upgrades driven by the age of components. Thirty-three percent of readers are more than six years old while thirty percent of controllers and 24 percent of software are also six years old. It is network security upgrades that will procced rapidly with 28 percent planned in less than a year.
Disparate systems often run across the same campus and with none of them integrated, operators face multiple log-in procedures merely to respond to a single incident. With age comes unreliability. Forty-two percent of respondents said their current system malfunctions between two and five times annually while 22 percent reported monthly malfunctions.
The survey reveals that access control user experiences for faculty and students must be improved. This is followed by need to exploit currently missing features that are available in newer systems. The research shows that administrators are most inconvenienced by how user credentials are issued and managed. This is followed by inability to synchronise information across disparate security components.
It comes with the territory that student populations mean recurring administrative tasks. Constant enrolments mean frequent managing of credentials and privileges. A new term means major changes with little institutional memory over time. End-user inconveniences include inability to use mobile devices as a credential.
Students are more likely than most to be inventive in circumventing systems that inconvenience them. A door propped open or window left unlocked is predictable if a system is difficult to use. Scalability and being able to use smartphones and wearables as credentials are on many wish lists. After the obvious obstacle of cost, impediments to upgrades include lack of compelling ROI and operational disruption. The value of two-factor authentication is widely appreciated. Half of respondents already use it or will implement it soon
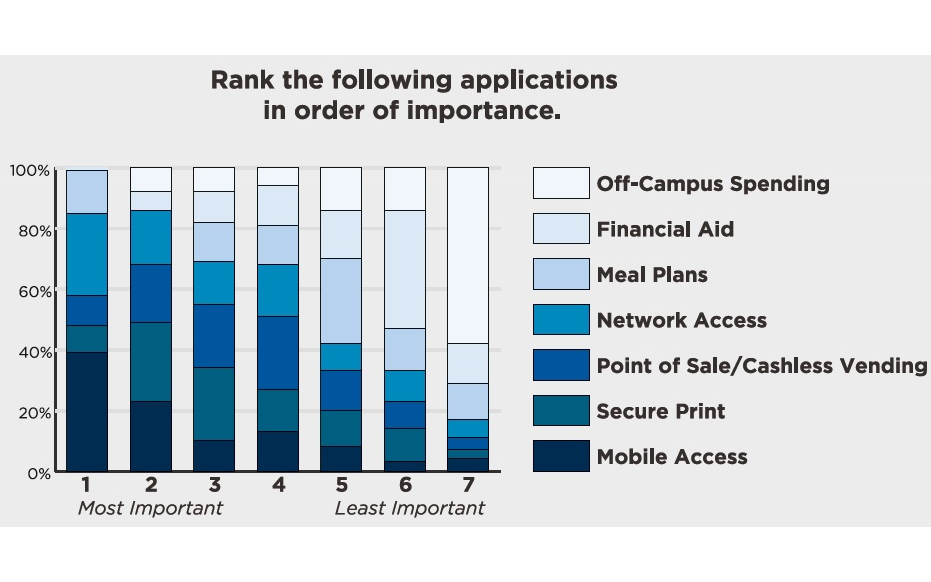
Higher education is receptive to multi-use applications. Colleges are enterprising in having students use cards as much as possible with applications including locking bicycles. There are card technologies for checking out books and cashless vending. There is a challenge to standardize with a single credential interface which produces both economies and logistical benefits.
Top among requirements is mobile access control. Anybody of student age has grown up with a smartphone. Using a phone and wearable technology as the credential device is a goal for product developers. This approach will reduce abuse; a student might lend a card to a colleague but not their phone. There are obvious savings in not having to issue cards.
About the survey
The survey was conducted at campuses of various sizes. The respondents had a variety of security and IT roles and were diverse in age with the largest share being between 45 and 65. Budget sizes varied although 47 percent had a budget of below $250,000.
Discover all the findings from the survey in HID Global’s White Paper.
Download your copy at https://hid.gl/CEM